[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]  Tagger [@TaggerAI](/creator/twitter/TaggerAI) on x 40.6K followers Created: 2025-07-24 14:10:03 UTC In today’s AI economy, high‑quality data is scarce, expensive to acquire and label, yet distressingly easy to copy, leak, or alter. Enterprises pour millions into building or purchasing datasets, then spend millions more on security infrastructure - only to remain exposed to theft or misuse. Legal protections exist, but history shows that bad actors still steal data, and proving misconduct (think Waymo’s protracted trade‑secret battle with Uber) is slow, complex, and ruinously costly. #DeCorp’s on‑chain Data Authentication Protocol eliminates these vulnerabilities at the root. Every datapoint is immutably recorded and safeguarded by the consensus mechanisms. Any unauthorized change is impossible to hide, instantly traceable, and - if attempted- provides cryptographic evidence that stands up in court. 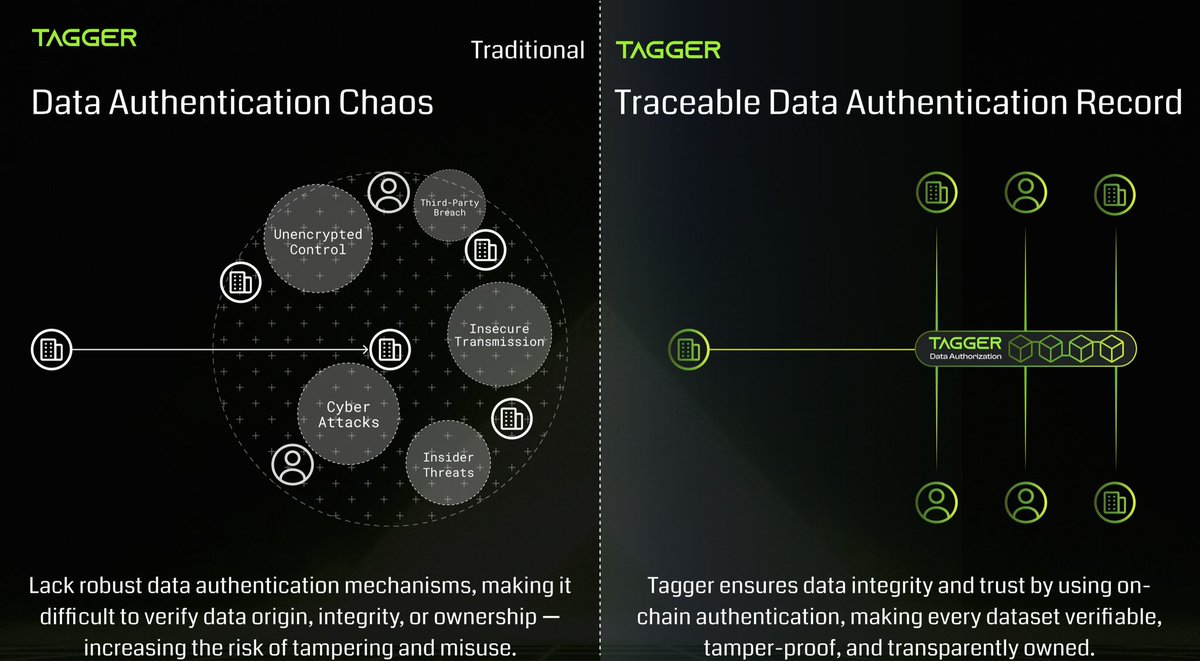 XXXXXX engagements  **Related Topics** [coins ai](/topic/coins-ai) [tagger](/topic/tagger) [Post Link](https://x.com/TaggerAI/status/1948385190591730055)
[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]
 Tagger @TaggerAI on x 40.6K followers
Created: 2025-07-24 14:10:03 UTC
Tagger @TaggerAI on x 40.6K followers
Created: 2025-07-24 14:10:03 UTC
In today’s AI economy, high‑quality data is scarce, expensive to acquire and label, yet distressingly easy to copy, leak, or alter.
Enterprises pour millions into building or purchasing datasets, then spend millions more on security infrastructure - only to remain exposed to theft or misuse. Legal protections exist, but history shows that bad actors still steal data, and proving misconduct (think Waymo’s protracted trade‑secret battle with Uber) is slow, complex, and ruinously costly.
#DeCorp’s on‑chain Data Authentication Protocol eliminates these vulnerabilities at the root. Every datapoint is immutably recorded and safeguarded by the consensus mechanisms. Any unauthorized change is impossible to hide, instantly traceable, and - if attempted- provides cryptographic evidence that stands up in court.

XXXXXX engagements