[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]  Tio Red Octo 🐙 W. κρυπτός 𒀭𒀀𒉣𒈾 🜃Φ🌹🇵🇸𓂀 🪬 [@Gandalf_ElPulpo](/creator/twitter/Gandalf_ElPulpo) on x 10.9K followers Created: 2025-07-19 02:20:57 UTC 🥤🐙 National Security Agency/Central Security Service (NSA/CSS @NSAGov) and - Network Warfare & U.S. Strategic Command Joint Functional Component Command - Network Warfare (JFCC-NW) National Initiative Protection Program - Sentry Eagle "TOP SECRET//COMINT//NOFORN/20310524 DRAFT (S) NSA/CSS/JFCC-NW National Initiative Brief Sheet X. (S/NF) You are being indoctrinated on SENTRY EAGLE, the NSA/CSS and JFCC-NW's compartmented program protecting the highest and most sensitive level of information related to NSA/CSS's and JFCC-NW's support to the U.S. Government's efforts to protect America's cyberspace. America's cyberspace is the combination of U.S. National Security Systems, Military Systems, Intelligence Systems, Federal Government Systems, Critical Infrastructure Systems and all other U.S. systems (private industry, academia and private citizen.) X. (S/NF) NSA/CSS's effort to protect America's cyberspace encompasses the combination of all abilities to detect nation and non-nation attacks on U.S. cyberspace via active and passive SIGINT and Information Assurance means. JFCC-NW's effort to protect America's cyberspace encompasses the efforts to plan, synchronize, and when tasked, attack an adversary's cyber space via Computer Network Attack. The combination of these two efforts constitutes NSA/CSS's and JFCC-NW's Combined Computer Network Operations (CNO) Secrets. X. (TS/SI/NF) In order for NSA/CSS and JFCC-NW to accomplish, along with other U.S. and foreign government agencies/elements, the protection of America's cyberspace, NSA/JFCC-NW must combine the full capabilities of authorized Computer Network Operations (SIGINT, Computer Network Exploitation (CNE), Information Assurance, Computer Network Defense (CND), and Network Warfare, Computer Network Attack (CNA)) and all supporting activities. X. (TS/SI/NF) SENTRY EAGLE and its subordinate programs protect the combined facts related to NSA/CSS and JFCC-NW's programs to conduct CNO operations. It encompasses the most sensitive aspects of NSA/CSS's: relationships with industry (U.S. and foreign) and the U.S. Information Operations/CNO community; ability to exploit enciphered communications; ability to conduct CNE; ability to conduct CND; and, relationships with Human Intelligence (HUMINT) Agencies. X. (TS/SI/NF) These NSA/CSS and JFCC-NW Core CNO Secrets are being provided to you based upon your "need to know" as determined by the Director, NSA/Chief, Central Security Service and Commander, JFCC-NW. While many of the facts in this briefing are contained in separate NSA/CSS Exceptionally Controlled Information (ECI) or DOD Special Access Programs (SAPs) structures, no other program combines the totality of all these facts into one overarching program. The facts contained in this program constitute a combination of the greatest number of highly sensitive facts related to NSA/CSS's overall cryptologic mission. As such, depending upon TOP SECRET//COMINT//NOFORN/20310524 DRAFT" 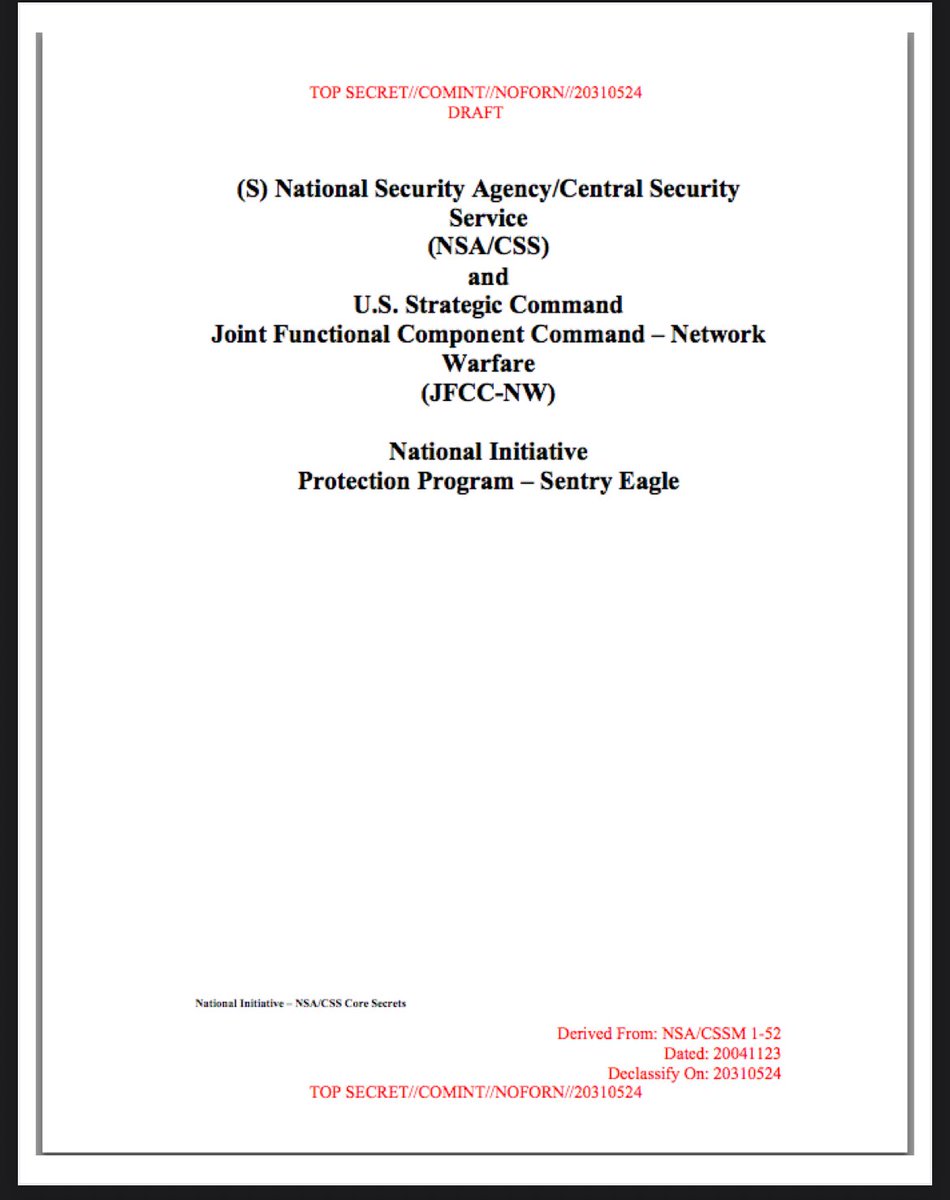 XXX engagements  **Related Topics** [eagle](/topic/eagle) [national security](/topic/national-security) [Post Link](https://x.com/Gandalf_ElPulpo/status/1946394799390818399)
[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]
 Tio Red Octo 🐙 W. κρυπτός 𒀭𒀀𒉣𒈾 🜃Φ🌹🇵🇸𓂀 🪬 @Gandalf_ElPulpo on x 10.9K followers
Created: 2025-07-19 02:20:57 UTC
Tio Red Octo 🐙 W. κρυπτός 𒀭𒀀𒉣𒈾 🜃Φ🌹🇵🇸𓂀 🪬 @Gandalf_ElPulpo on x 10.9K followers
Created: 2025-07-19 02:20:57 UTC
🥤🐙 National Security Agency/Central Security Service (NSA/CSS @NSAGov) and - Network Warfare & U.S. Strategic Command Joint Functional Component Command - Network Warfare (JFCC-NW)
National Initiative Protection Program - Sentry Eagle
"TOP SECRET//COMINT//NOFORN/20310524 DRAFT
(S) NSA/CSS/JFCC-NW National Initiative Brief Sheet
X. (S/NF) You are being indoctrinated on SENTRY EAGLE, the NSA/CSS and JFCC-NW's compartmented program protecting the highest and most sensitive level of information related to NSA/CSS's and JFCC-NW's support to the U.S. Government's efforts to protect America's cyberspace. America's cyberspace is the combination of U.S. National Security Systems, Military Systems, Intelligence Systems, Federal Government Systems, Critical Infrastructure Systems and all other U.S. systems (private industry, academia and private citizen.)
X. (S/NF) NSA/CSS's effort to protect America's cyberspace encompasses the combination of all abilities to detect nation and non-nation attacks on U.S. cyberspace via active and passive SIGINT and Information Assurance means. JFCC-NW's effort to protect America's cyberspace encompasses the efforts to plan, synchronize, and when tasked, attack an adversary's cyber space via Computer Network Attack. The combination of these two efforts constitutes NSA/CSS's and JFCC-NW's Combined Computer Network Operations (CNO) Secrets.
X. (TS/SI/NF) In order for NSA/CSS and JFCC-NW to accomplish, along with other U.S. and foreign government agencies/elements, the protection of America's cyberspace, NSA/JFCC-NW must combine the full capabilities of authorized Computer Network Operations (SIGINT, Computer Network Exploitation (CNE), Information Assurance, Computer Network Defense (CND), and Network Warfare, Computer Network Attack (CNA)) and all supporting activities.
X. (TS/SI/NF) SENTRY EAGLE and its subordinate programs protect the combined facts related to NSA/CSS and JFCC-NW's programs to conduct CNO operations. It encompasses the most sensitive aspects of NSA/CSS's: relationships with industry (U.S. and foreign) and the U.S. Information Operations/CNO community; ability to exploit enciphered communications; ability to conduct CNE; ability to conduct CND; and, relationships with Human Intelligence (HUMINT) Agencies.
X. (TS/SI/NF) These NSA/CSS and JFCC-NW Core CNO Secrets are being provided to you based upon your "need to know" as determined by the Director, NSA/Chief, Central Security Service and Commander, JFCC-NW. While many of the facts in this briefing are contained in separate NSA/CSS Exceptionally Controlled Information (ECI) or DOD Special Access Programs (SAPs) structures, no other program combines the totality of all these facts into one overarching program. The facts contained in this program constitute a combination of the greatest number of highly sensitive facts related to NSA/CSS's overall cryptologic mission. As such, depending upon
TOP SECRET//COMINT//NOFORN/20310524 DRAFT"

XXX engagements
Related Topics eagle national security