[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]  0𝙿𝚃𝚃𝙸𝙼𝚄𝚂 🦺 | 魚男 🐟 [@0pttimus](/creator/twitter/0pttimus) on x 2956 followers Created: 2025-07-18 15:27:34 UTC 🏴☠️ MyTonWallet Air Security Bounty Program For ethic hackers & security researchers 🤨 Prize fund: Up to $XXXXXX Deadline: X August 2025 at 14:00 CET X. The Task We’re inviting security researchers to audit MyTonWallet Air—our new native app for iOS and Android. Your mission: find and responsibly disclose security vulnerabilities that could compromise user assets, privacy, or overall security through code analysis. This is a public security bounty program focused on identifying critical, high-impact issues before full release. How to Access the Code? iOS and Android source code for MyTonWallet Air is available here; X. What Counts as a Valid Vulnerability? We’re specifically interested in serious vulnerabilities such as: • Unauthorized access to wallets or private data • Bypassing authentication or authorization flows • Transaction forgery or signing without user consent • Cryptographic failures • Anything leading to token theft or DoS Minor UI glitches, layout issues, typos, performance lags, or non-security-related behavior should be submitted via the QA Contest; X. Submission Guidelines Please include in your report: • Clear description of the vulnerability • Code location and affected components • Clear reproduction steps or proof-of-concept • Potential impact • Screenshots or other content if applicable Submit your reports directly to @mysafewallet for all security disclosures. X. Evaluation Criteria Our team will assess each submission based on: · Severity and potential impact · Reproducibility and clarity of reporting · Quality of documentation or proof-of-concept · Responsible disclosure and ethical conduct Only valid, original, and verifiable submissions will be considered for rewards. X. Rewards & Contact Rewards will be distributed based on the severity and quantity of vulnerabilities found. If multiple participants discover the same vulnerability, the reward will be distributed as follows: XX% to the first reporter, and the remaining XX% shared equally among all reporters of the same issue. Send your reports directly to @mysafewallet—top submissions will be rewarded accordingly. 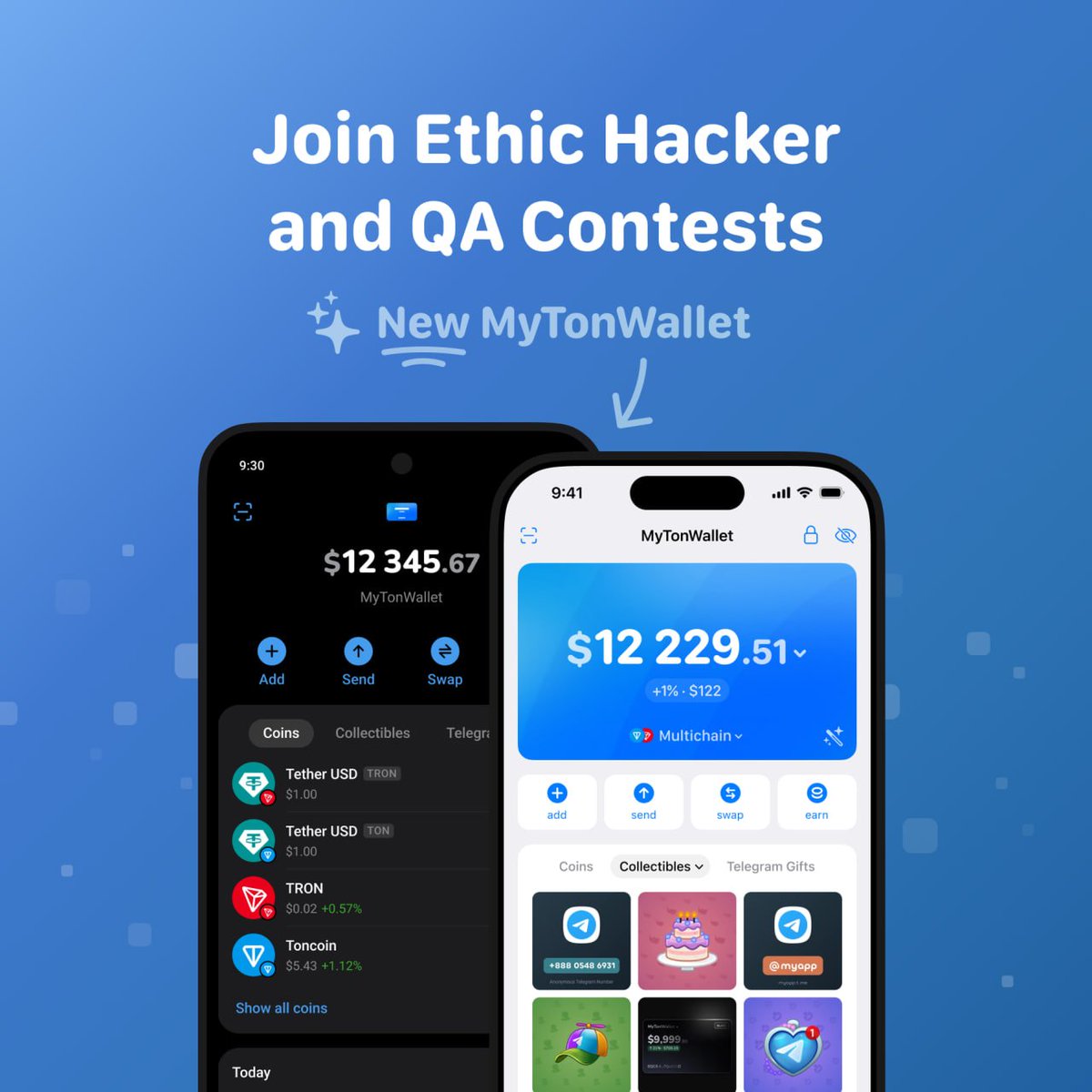 XX engagements  **Related Topics** [coins privacy](/topic/coins-privacy) [android](/topic/android) [ios](/topic/ios) [cet](/topic/cet) [bounty](/topic/bounty) [Post Link](https://x.com/0pttimus/status/1946230371265446364)
[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]
 0𝙿𝚃𝚃𝙸𝙼𝚄𝚂 🦺 | 魚男 🐟 @0pttimus on x 2956 followers
Created: 2025-07-18 15:27:34 UTC
0𝙿𝚃𝚃𝙸𝙼𝚄𝚂 🦺 | 魚男 🐟 @0pttimus on x 2956 followers
Created: 2025-07-18 15:27:34 UTC
🏴☠️ MyTonWallet Air Security Bounty Program
For ethic hackers & security researchers 🤨
Prize fund: Up to $XXXXXX
Deadline: X August 2025 at 14:00 CET
X. The Task
We’re inviting security researchers to audit MyTonWallet Air—our new native app for iOS and Android.
Your mission: find and responsibly disclose security vulnerabilities that could compromise user assets, privacy, or overall security through code analysis.
This is a public security bounty program focused on identifying critical, high-impact issues before full release.
How to Access the Code?
iOS and Android source code for MyTonWallet Air is available here;
X. What Counts as a Valid Vulnerability?
We’re specifically interested in serious vulnerabilities such as:
• Unauthorized access to wallets or private data • Bypassing authentication or authorization flows • Transaction forgery or signing without user consent • Cryptographic failures • Anything leading to token theft or DoS
Minor UI glitches, layout issues, typos, performance lags, or non-security-related behavior should be submitted via the QA Contest;
X. Submission Guidelines
Please include in your report:
• Clear description of the vulnerability • Code location and affected components • Clear reproduction steps or proof-of-concept • Potential impact • Screenshots or other content if applicable
Submit your reports directly to @mysafewallet for all security disclosures.
X. Evaluation Criteria
Our team will assess each submission based on:
· Severity and potential impact · Reproducibility and clarity of reporting · Quality of documentation or proof-of-concept · Responsible disclosure and ethical conduct
Only valid, original, and verifiable submissions will be considered for rewards.
X. Rewards & Contact
Rewards will be distributed based on the severity and quantity of vulnerabilities found.
If multiple participants discover the same vulnerability, the reward will be distributed as follows: XX% to the first reporter, and the remaining XX% shared equally among all reporters of the same issue.
Send your reports directly to @mysafewallet—top submissions will be rewarded accordingly.

XX engagements
Related Topics coins privacy android ios cet bounty