[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]  Trend Micro Research [@TrendMicroRSRCH](/creator/twitter/TrendMicroRSRCH) on x 51.9K followers Created: 2025-07-10 05:00:00 UTC Cybercriminals exploit Docker APIs and the Tor network to mine cryptocurrency undetected. This stealthy method targets cloud-heavy industries like technology, finance, and healthcare. Full details in our blog: ⬇️ 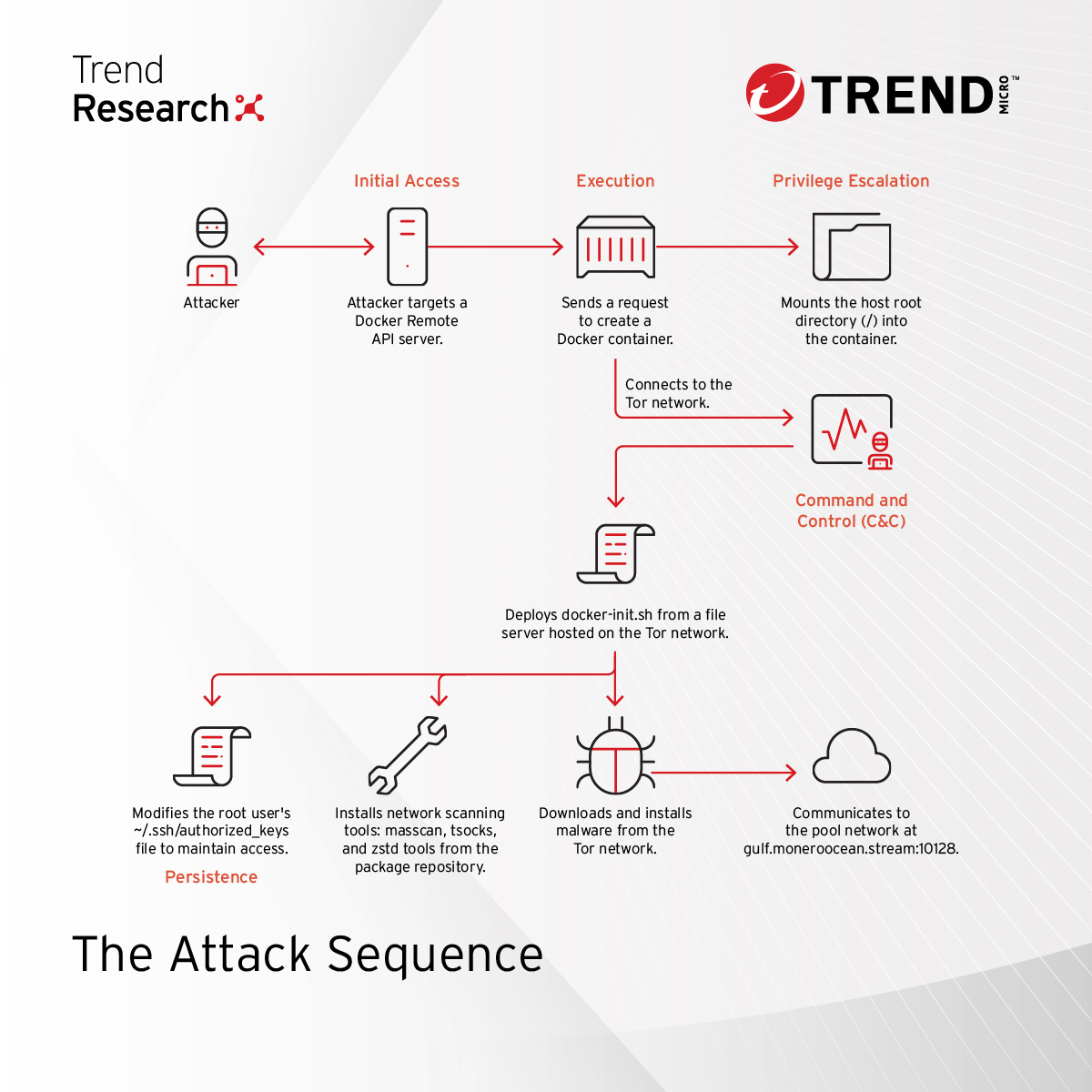 XXX engagements  **Related Topics** [coins healthcare](/topic/coins-healthcare) [finance](/topic/finance) [stocks technology](/topic/stocks-technology) [cryptocurrency](/topic/cryptocurrency) [$4704t](/topic/$4704t) [Post Link](https://x.com/TrendMicroRSRCH/status/1943173338265686436)
[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]
 Trend Micro Research @TrendMicroRSRCH on x 51.9K followers
Created: 2025-07-10 05:00:00 UTC
Trend Micro Research @TrendMicroRSRCH on x 51.9K followers
Created: 2025-07-10 05:00:00 UTC
Cybercriminals exploit Docker APIs and the Tor network to mine cryptocurrency undetected. This stealthy method targets cloud-heavy industries like technology, finance, and healthcare.
Full details in our blog: ⬇️

XXX engagements
Related Topics coins healthcare finance stocks technology cryptocurrency $4704t