[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]  Finance Trending [@FinTrending](/creator/twitter/FinTrending) on x 3305 followers Created: 2025-06-27 07:19:19 UTC 🚨🇺🇸 $199K 𝙇𝙊𝙎𝙏 𝙄𝙉 𝙐𝙎𝘿𝙏 - 𝘼𝙙𝙙𝙧𝙚𝙨𝙨 𝙋𝙤𝙞𝙨𝙤𝙣𝙞𝙣𝙜 𝙨𝙘𝙖𝙢 𝙝𝙞𝙩𝙨 𝙖𝙜𝙖𝙞𝙣 Another day, another wallet drained. One unlucky crypto user just lost $XXXXXXX in USDT - not from a hack, but a deadly simple address poisoning trick. Here’s how it works: The scammer sends a $X transaction from a lookalike address that closely matches one in your recent history. When the victim copy-pastes the wrong address by mistake… boom. Funds gone. No way back. @web3_antivirus has tracked multiple similar scams, with most trails pointing to one persistent wallet-drainer who’s been farming this method for months. This is social engineering XXX - and it’s working. ⚠️ Copy-paste ≠ safe. ⚠️ Block explorers won’t save you. ⚠️ The bots are getting smarter. If you're transacting in crypto, you are the last line of defense. 𝙁𝙞𝙣𝙖𝙣𝙘𝙞𝙖𝙡 𝙞𝙢𝙥𝙖𝙘𝙩: • $199K lost in a single USDT transaction to a scammer • Growing trend of address poisoning as phishing evolves • Major risk for high-frequency traders and airdrop hunters • Wallet hygiene now critical for retail + pro traders alike • Web3 security tools gaining urgency (watchlists, transaction alerts, etc.) Source: @web3_antivirus 𝙁𝙞𝙣𝙖𝙣𝙘𝙚 𝙛𝙧𝙚𝙨𝙝, 𝙣𝙤 𝙢𝙤𝙧𝙚 𝙨𝙩𝙧𝙚𝙨𝙨. 𝙄𝙣 𝙖 𝙬𝙤𝙧𝙡𝙙 𝙩𝙝𝙖𝙩’𝙨 𝙩𝙧𝙚𝙣𝙙𝙞𝙣𝙜, 𝙛𝙤𝙡𝙡𝙤𝙬 𝙁𝙞𝙣𝙖𝙣𝙘𝙚 𝙏𝙧𝙚𝙣𝙙𝙞𝙣𝙜. #FinanceTrending 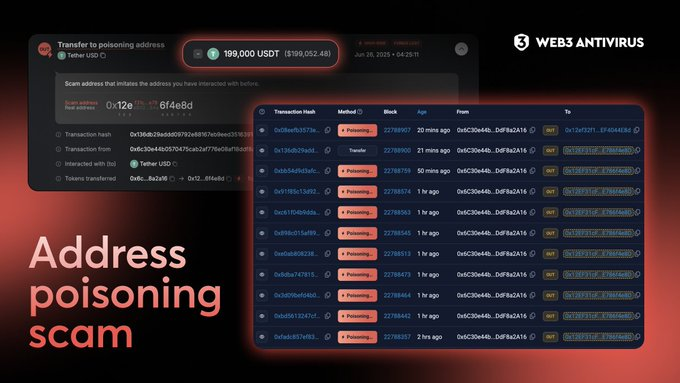 XXX engagements  **Related Topics** [hack](/topic/hack) [usdt](/topic/usdt) [$199k](/topic/$199k) [finance](/topic/finance) [Post Link](https://x.com/FinTrending/status/1938497353142390844)
[GUEST ACCESS MODE: Data is scrambled or limited to provide examples. Make requests using your API key to unlock full data. Check https://lunarcrush.ai/auth for authentication information.]
 Finance Trending @FinTrending on x 3305 followers
Created: 2025-06-27 07:19:19 UTC
Finance Trending @FinTrending on x 3305 followers
Created: 2025-06-27 07:19:19 UTC
🚨🇺🇸 $199K 𝙇𝙊𝙎𝙏 𝙄𝙉 𝙐𝙎𝘿𝙏 - 𝘼𝙙𝙙𝙧𝙚𝙨𝙨 𝙋𝙤𝙞𝙨𝙤𝙣𝙞𝙣𝙜 𝙨𝙘𝙖𝙢 𝙝𝙞𝙩𝙨 𝙖𝙜𝙖𝙞𝙣
Another day, another wallet drained.
One unlucky crypto user just lost $XXXXXXX in USDT - not from a hack, but a deadly simple address poisoning trick.
Here’s how it works:
The scammer sends a $X transaction from a lookalike address that closely matches one in your recent history. When the victim copy-pastes the wrong address by mistake… boom. Funds gone. No way back. @web3_antivirus has tracked multiple similar scams, with most trails pointing to one persistent wallet-drainer who’s been farming this method for months.
This is social engineering XXX - and it’s working.
⚠️ Copy-paste ≠ safe. ⚠️ Block explorers won’t save you. ⚠️ The bots are getting smarter.
If you're transacting in crypto, you are the last line of defense. 𝙁𝙞𝙣𝙖𝙣𝙘𝙞𝙖𝙡 𝙞𝙢𝙥𝙖𝙘𝙩: • $199K lost in a single USDT transaction to a scammer • Growing trend of address poisoning as phishing evolves • Major risk for high-frequency traders and airdrop hunters • Wallet hygiene now critical for retail + pro traders alike • Web3 security tools gaining urgency (watchlists, transaction alerts, etc.) Source: @web3_antivirus
𝙁𝙞𝙣𝙖𝙣𝙘𝙚 𝙛𝙧𝙚𝙨𝙝, 𝙣𝙤 𝙢𝙤𝙧𝙚 𝙨𝙩𝙧𝙚𝙨𝙨. 𝙄𝙣 𝙖 𝙬𝙤𝙧𝙡𝙙 𝙩𝙝𝙖𝙩’𝙨 𝙩𝙧𝙚𝙣𝙙𝙞𝙣𝙜, 𝙛𝙤𝙡𝙡𝙤𝙬 𝙁𝙞𝙣𝙖𝙣𝙘𝙚 𝙏𝙧𝙚𝙣𝙙𝙞𝙣𝙜. #FinanceTrending

XXX engagements